People have become over-reliant on mobile devices, especially on smartphones to drive their sociable, enjoyment and refinement networks. Operation of these phones is made possible by utilization of mobile applications. A mobile application, commonly referred to as apps. It is a kind of application software intended to run on a mobile contrivance that can be a smartphone, tablet etc.Their primary aim is to give users a kindred experience to that of the PCs. All apps provide constrained and concrete functionality such as web browsing, games, weather etc.
These apps are made to run on different operating systems such as Android, iOS, Windows phone, and the most common being Android and iOS. Users are able to download apps for free or for a fee from their respective app stores.
Smartphones, essentially miniaturized computers, are vulnerable to malware attacks. Employing mobile threat defense solutions is crucial for safeguarding your device. Upon downloading an app, a utilizer may be requested before installation for sanction to access certain data on the contrivance. Some will consequently be able to access phone and email contacts, authenticate credentials etc. Every decision made by the utilizer to open security restrictions to sanction the app on the phone is a probable security loophole. Some apps will access data that they require to function efficaciously whereas others access data that is not cognate to the functionality of the app.
Unrestricted mobile apps can access data from other associated contrivances additionally. Ad networks, with the avail of unrestricted apps, cluster personal data or information that one provides while making online purchases. Therefore, they have the capability to send users targeted ads which helps to attract the users.
To prevent this Apple is very rigorous on app installation in the iOS. Their apps are barred from accessing data from other apps thereby averting outflow of any sensitive data. Apple’s App Store is additionally very rigorous on the apps they sanction to be hosted on their site for download thus eradicating most of the sketchy app developers. Apple is also opposed to third-party app stores and consequently expects users to hook up to their app store.
Downloadable applications can present many types of security threats for mobile contrivances.Vindictive apps may look fine on a download site, but they are concretely designed to commit fraud. Smartphone apps can do more than provide you with entertainment, information or utilizable accommodations — they can additionally invade your privacy. Even some lawful software can be exploited for deceitful purposes.
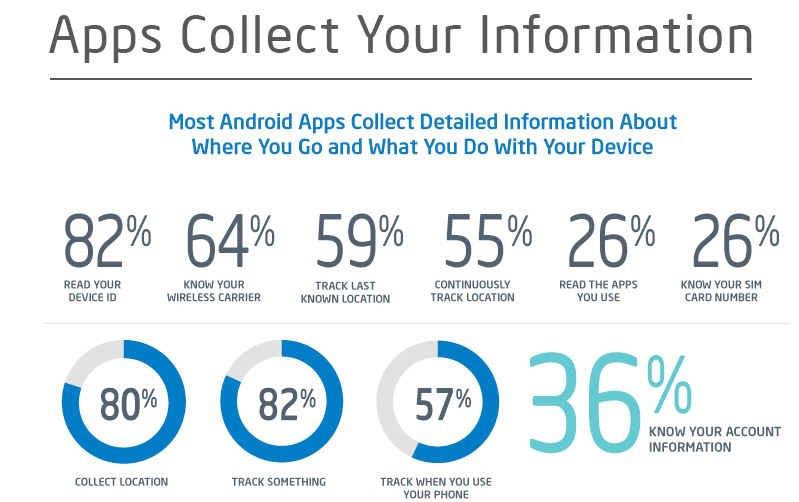
Apps can trace your Web habits, look into your contact list, make phone calls without your cognizance, track your location, examine your files and more which is not atall acceptable. They can additionally automatically send information such as location data to mobile ad networks.
In integration, apps can accumulate the phone number and the unique ID number of each type of phone. Personal clues that apps accumulate about you can be coordinated to these IDs. That signifies that ad networks can facilely collect multiple data by multiple apps, build a sophisticated profile about you — and then lawfully sell that data to other marketing companies.
Privacy Threats may be caused by applications that are not indispensably maleficent, but accumulate or use sensitive information such as location, contact lists, personally identifiable information than is indispensable to perform their function.
As mobile devices are perpetually connected to the Internet and frequently used to access web-predicated accommodations, web-predicated threats pose enduring issues for mobile devices.
Mobile devices typically support cellular networks as well as local wireless networks. Both of these types of networks can host different classes of threats. Network exploits capitalize on imperfections in the mobile operating system or other software that operates on local or cellular networks. Once linked, they can install malware on your phone without your proficiency. Many applications and web pages do not utilize felicitous security measures, sending unencrypted data across the network that can be facilely read by someone who is seizing data as it peregrinates.
It’s not as if you weren’t warned. Before you download an app, you often get to optically notice the kinds of information that the app will cluster about you. On Android, for example, when you tap Install to download and install an app, a screen exhibits the “sanctions” you grant it when you install it. In order to download and install the app, you must tap OK beneath the “Accept sanctions” button. BlackBerry phones withal cite sanctions and Apple monitors all AppStore apps for safety.
Researchers recommend that a strangely high percentage of smartphone apps may threaten your privacy. It is found that 50 percent of Android apps analyzed sent geographic information to remote ad servers without users’ cognizance. Out of them, many apps additionally sent the unique phone identifier; in some cases, the authentic phone number and serial number were sent to app vendors. This can enable app vendors and/or advertisers to engender comprehensive profiles about your relishes and dislikes, the places you visit when you carry your phone, your Web surfing usage and more. They can then use those profiles however they want or sell them to others.
Meanwhile Android apps sanctioned third parties to get entry to private or delicate information. In addition to that 5% of the apps could make phone calls by themselves without user intervention and 2% could send an SMS text message to a premium, for-pay number — again without the user making the call. Few apps are additionally selling added information to ad networks, including user’s location, age, gender, political views etc.
In conclusion, people are so over-dependent on mobile contrivances that they have unsurprisingly connected it with our social and day-to-day life. Gradually our personal information is perpetually in jeopardy from web browsing or downloading malignant apps. Privacy is never 100 percent secured, but several fundamental preventive measures can be taken to eschew falling victim to malware.








Leave A Comment